Pubic
Relations
You have to move from your existing
facility to a new one, and you need to do it over the weekend, with
no down time for your employees. You have clients that are depending
on orders filled, and you need to see that process not impeded. Your
facility has mechanical equipment and machinery that is essential
for your operation, and it needs to be disconnected, moved, and set
up in an orderly fashion to insure high productivity. In addition,
you only have the weekend to make this happen, or else it could cost
you clients and business. Who will you contact? This is the type of
project the Prism Consulting has done, and can do for clients. All
this requires immediate coordination with people for the most
efficient operations. Our customerís needs are our
objective.
You have a family, and want to build a house. In
the process you find out that you are responsible for making road
improvements. After several months of the process, and knowing that
you have already contracted and seen the construction youíre your
new home begin, you find out that "road improvements" are now
defined as building a new road and making it comply with State
standards. Who are you going to contact? You have never built a road
before, and you have a wife, small children, a full time job, and
did not ever plan to be a road builder? This is the type of project
that Prism Consulting helps with. We coordinate with local, and
state officials to help walk you through the process. It is never
the goal to circumvent the process, but to guide you through it as
quickly as possible. We will coordinate activities and interact with
decision makers for the best and quickest solution. Team work is the
objective and always the scope.
Biometric Technology has been
in existence for years. It has been implemented in various
operations in commercial, government and private sectors. The
various forms of biometrics can take the place of pin numbers for
ATM cards, keys for access to automobiles, and authentication for
access of information. It can be vital for the issue of liability in
business and industry. Below is some information on the technology.
Prism Consulting provides training on this technology with total
solutions for implementing biometrics for your needs.
Voice Security Technology
Voice security technology can be easily inserted
into most applications because most applications have embedded
processors. This is important because most consumer products must
provide the most features for the lowest cost. Adding additional
hardware can sometimes make your product non-competitive. Cellular
phone technology is an example of such an application.
The
diagram below shows the basic hardware used in voice security. The
userís voice is read into the embedded processor through a
microphone and an analog-to-digital converter (ADC). The embedded
processor transforms the users voice into templates that can be
compared with previously recorded templates of the userís voice. If
the voice security test is passed, the embedded processor enables
the product to function. If the voice security test is failed, an
indicator (visual or verbal) tells the user to try
again.
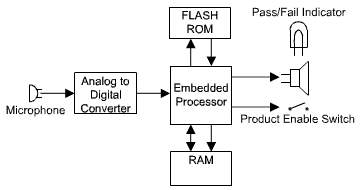
Figure 1: Required Voice Security
Hardware
A cell phone has all of the needed
functions given above. All they lack is the voice security algorithm
to run on their hardware!
There are several ways that the
voice security algorithm could be implemented on a cell phone. One
method is to use a power-on enabling function similar to what exists
in phones today. Current phones have a security feature when the
customer turns on the phone they must enter a Personal
Identification Number (PIN) to enable the phone. Instead of a PIN,
the embedded processorís program could be modified to implement the
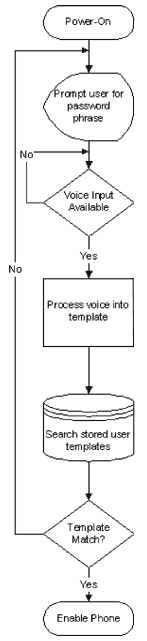
voice security algorithm as shown below.
During power-up
sequences, the amount of processing done by the embedded processor
is minimal. Most of the time is spent waiting for user input such as
keypad entry for the PIN. This time could be used instead to prompt
the user for a voice password and monitor the microphone to capture
the voice input. Upon receiving the voice input, the embedded
processor transforms the data input into a voice template for
comparison against the user database. Even the smallest of embedded
processors can perform this transform in a time-effective manner to
prevent the user from excessive waits during voice validation. If
the voice template matches, the phone is then enabled. If the voice
template does not match, the user can try again.
All this
can be done on the embedded processor that is usually not fully
loaded during this time. This application only adds about 4-8 Kbytes
of new code to the product. Considering cell phones have games and
other toys running on the embedded processor, this will not require
any additional parts to be added to the phone.
Application
Ideas:
Facility Access: This system can emulate
existing peripherals used in access to facilities locations that use
scan card or smart card technology.
Computer Access: Speech
verification can be used to control access to computers.
Time
Clock: When a person comes to work, rather then punch a time clock,
speaking into a computerized system can integrate with payroll
systems, making it easier to account for activity.
ATM Card:
Utilizing speech versus pin numbers decreases administrative costs
on ATM cards, and also increases security.
Account
Authorization: Account managers have to verify a client prior to
giving out personal information on accounts. With speech
verification, fraudulent access of information is decreased, and it
assures clients and customers that their personal information will
be protected.
Developing Technology: You may have
applications that can utilize speech verification technology. We
have engineers that can design an application to be utilized in many
different applications.






